29
Aug
Microsoft Azure confidential ledger: Enhancing customer trust in Azure’s hardware supply chain
Microsoft Azure hardware’s security posture is foundational to the security promises we make to our customers. The supply chain of Microsoft Azure servers relies on a multifaceted and complex ecosystem of partners across silicon production, assembly, systems integration, transit, and operationalization in data centers. Multiple interaction points across this supply chain pose significant threats to the security and integrity of an Azure server landing in production. These risks include firmware tampering, hardware tampering, installation of malicious code or spyware, weakened security controls, and many more. We at Microsoft believe it is critical to build mechanisms to proactively detect and remediate such issues during the early phases of product development or before servers dock in a data center.
Hardware Root-of-Trust (RoT) devices such as Cerberus and Trusted Platform Module are the cornerstone for establishing foundational trust on hardware components in our cloud. This ensures the authenticity and integrity of these components and their firmware with traceability all the way back to silicon manufacturing. The best way to accomplish our objective is to verify “provenance” of our servers throughout their lifecycle from factory to production using hardware RoT device identities. During the silicon manufacturing process, the device identity is securely extracted and annotated to uniquely identify trusted devices. This mitigates the risk of “rogue” devices finding their way into the Azure fleet undetected (Figure 1). Lenovo is one of our leading supplier partners that are pushing the boundaries of secure supply chain with us.
To further protect these hardware RoT identities on which we anchor the chain of trust, we leverage the power of enclaves and the Confidential Consortium Framework with Microsoft Azure confidential ledger to integrity-protect our supplier provenance database. Learn more about our firmware integrity protections.
Azure confidential ledger integrity protects existing databases and applications by acting as a point-in-time source of truth which provides cryptographic proofs in verification scenarios. Specifically, stored data is not only immutable and tamper-proof in the append-only ledger but is also independently verifiable. It is also beneficial as a repository of audit trails or records that need to be kept intact and selectively shared with certain personas. Data logged in the ledger remains immutable, privacy-enhanced, and protected from insider threats within an organization or even the cloud provider.
In this scenario, Azure confidential ledger provides industry-leading tamper-evidence capabilities to determine if any unauthorized manipulations have occurred with these sensitive device identities. At different points in time, verification checks are executed against the Azure confidential ledger to ensure that the data is consistent and pristine. Using this technology also mitigates tampering risks from highly privileged Azure operators.
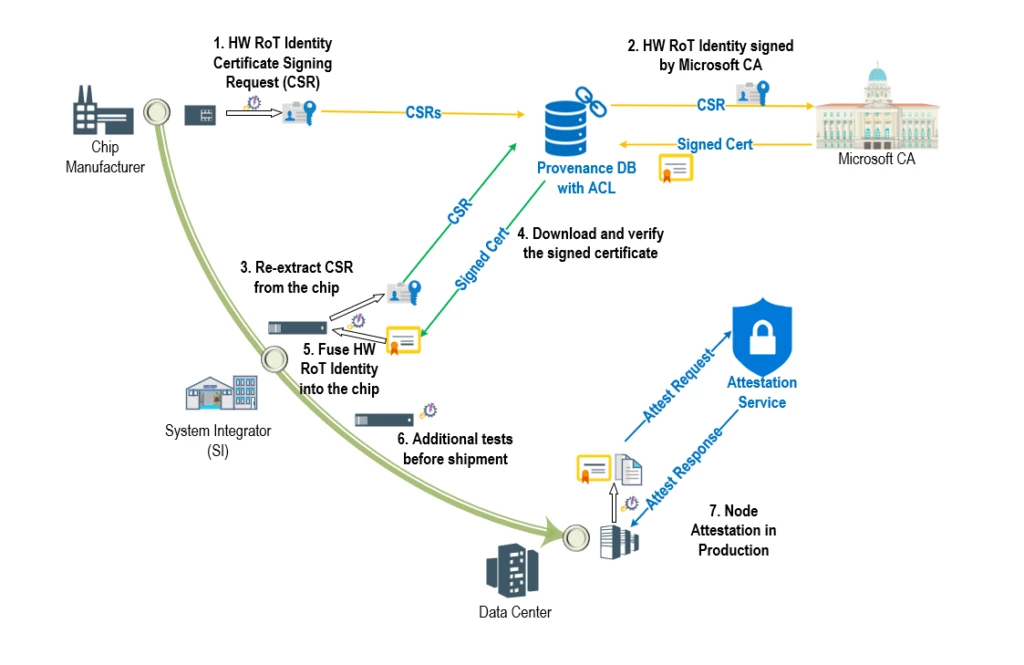
Azure confidential ledger is used to light up a critical infrastructure security scenario—Project Odyssey. Project Odyssey aims to cryptographically verify the provenance of hardware RoT devices (attached to servers) as they undertake their journey from OEM floors to Microsoft Azure data centers and throughout their production lifecycle. As part of the manufacturing workflow, suppliers upload a signed manifest of hardware RoT identities into a trusted ‘provenance database’ that uses tamper-evident Azure confidential ledger integration. As the devices are assembled into components, blades, and racks, their identities can be verified at each step of the supply chain process. After long journeys by air, land, and sea, the assembled racks arrive at Microsoft Data Centers where they undergo additional checks to ensure that they were not tampered with during transit. Finally, when a server is ready for production, it undergoes attestation where its hardware RoT identity can be re-verified before allowing it to join the production environment and host customer workloads. Servers are expected to undergo this process periodically ensuring that the hardware components stay compliant throughout their lifecycle, thereby ensuring that malicious and unauthorized swapping of blades and motherboards is detected, and non-compliant servers can be tagged for eviction, investigation, and remediation.
This is only one piece of our overall hardware security story. Microsoft Azure has developed comprehensive security requirements to enable security capabilities such as secure boot, secure update, attestation, recovery, encryption, and telemetry to ensure Azure hardware is resilient to such attacks through robust capabilities around prevention, detection, and response.
Read more about how we secure Microsoft Azure’s hardware and firmware.
At Microsoft, a core part of our culture is leveraging the work of each other to deliver industry-leading security to our customers with a defense in-depth approach. Azure hardware device provenance and supply chain security is a fundamental building block of our foundational security stack. Through cryptographic provenance verification of Azure hardware via Project Odyssey and additional defense-in-depth protections of hardware device identities using Azure confidential ledger, we are setting the gold standard in cloud hardware supply chain security to benefit our customers.
“Lenovo’s key priority is to verify and ensure the end-to-end security and traceability for Microsoft cloud hardware. By implementing this process in both our component and system integration factories, not only can we trust that the hardware we receive from downstream ODM/OEM suppliers is secured and trusted, but we can add the Lenovo fingerprint data to the chain of trust, which helps assure Microsoft that the hardware received by data centers is fully secured and trustworthy.
Integrating this solution into the Lenovo global supply chain workflow was exceptionally smooth thanks to the thorough documentation and examples that the Microsoft team maintains on an ongoing basis. Assuring the integrity and traceability of data in Azure confidential ledger allows Lenovo to focus on process and product quality, without needing to spend extra development cycles working on an in-house security solution.”—James McFadden, Executive Director, Supply Chain Quality & Engineering, Lenovo.
Learn more
- Read about how Microsoft Azure confidential ledger protects the integrity of your data.
- Read about Microsoft Azure’s hardware and firmware security.
The post Microsoft Azure confidential ledger: Enhancing customer trust in Azure’s hardware supply chain appeared first on Azure Blog.